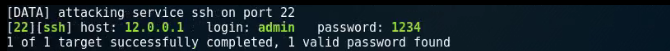
Hi Im Aravind Im Configured SSH On Router With Key Generated Using Rsa Algorithm with key size value 1024 bits ssh by default give login attempts for 3 times for 120 seconds so im trying brute force attack using some tools it will able crack the password of ssh
1024 bit key value 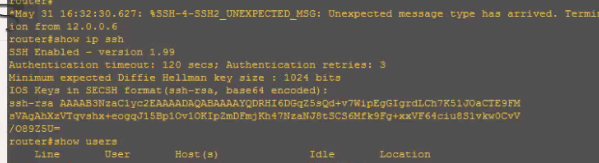
i Capture The Packet While Attacking malformed packet is appear when my bruteforce attack is success 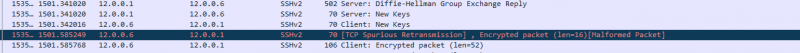
Parameters Inside Packet
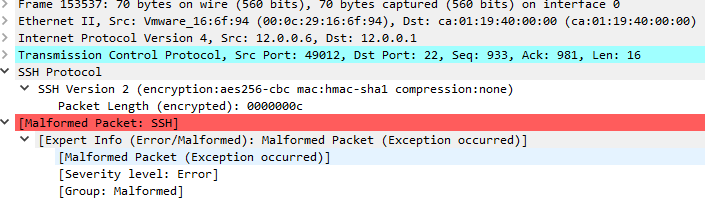
My Question Through The Attack We Can Decrypt The Key ?
There Is The Option Of Public And Private Key In RSA ?
If There Public Key And Private Key Options Are There How To Identify Is The Pubilc Key Or Private Key ?
why Default Authentication-retries Not Working ? (my tool Is Not Perform bruteforce Attack In Gain The Password With 3 Seconds )
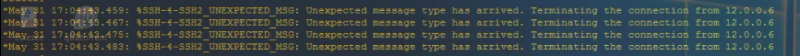
But In Router It Will Generate Logs Like These
When Im Performing Nmap Scan The Router Will Advertise RSA Hosts Keys How To Prevent Publish That Keys ?
Only My Applying Acl Then It Will Able To Prevent Attack im tried on real device Also
So Finally Im Question Is SSH Not Secure ???
- Total 2 Answers
- 3744
My Question Through The Attack We Can Decrypt The Key ?
There Is The Option Of Public And Private Key In RSA ?
If There Public Key And Private Key Options Are There How To Identify Is The Pubilc Key Or Private Key ?
I hope below cryptography mathematics will answer yours above questions and the rest I simply dont know :P and for the decrypting the key you need super computer and continues computation of 2 year minimum ....and as per the security policy most of the company changed the key after every month ...so even if you able to crack it , it might bee possible it was changed way back
The RSA algorithm requires a user to generate a key-pair, made up of a public key and a private key, using this asymmetry. Descriptions of RSA often say that the private key is a pair of large prime numbers (p, q), while the public key is their product n = p × q.
This is almost right; in reality there are also two numbers called d and e involved; e, which is used for encryption, is usually 65537, while d, which is used for decryption, is calculated from e, p, and q. The way we calculate d is straightforward to do but complicated to explain, and isn't really necessary for our purposes here. (Below, I'll give you some source code and a web app to automate the process so that you don't have to worry about it while solving the puzzle.) The end result is that d can be used to decrypt what e and n encrypt (using an operation called modular exponentiation), but only the private key's owner knows or can calculate d.
n is, indeed, published as part of the public key. Not only is the public allowed to know this number, but for security reasons the public key holder normally wants everyone to know it, to prevent someone else from maliciously impersonating them by giving out some other value of n
if need more try http://math.tut.fi/~ruohonen/MC.pdf
Cheers mate
- How can you guarantee a job for students who has no experience in Networking field?
- How to configure VPN between Cisco Router and ASA Firewall?
- How to configure RIPV2 with no auto summary?
- How to configure PAT (Port Address Translation)?
- How to configure Default Routing on Cisco Routers?
- What is the scope of CCNA course in India?
- What is scope of CCIE?
- How to remember 7 layers of OSI Model?
- How much salary can we get after doing CCNA course in Delhi Gurgaon?
- How many CCIE’s are there worldwide?
- Is it possible to pass CCIE Certification in 1st attempt?




