- Total 1 Answer
- 6037
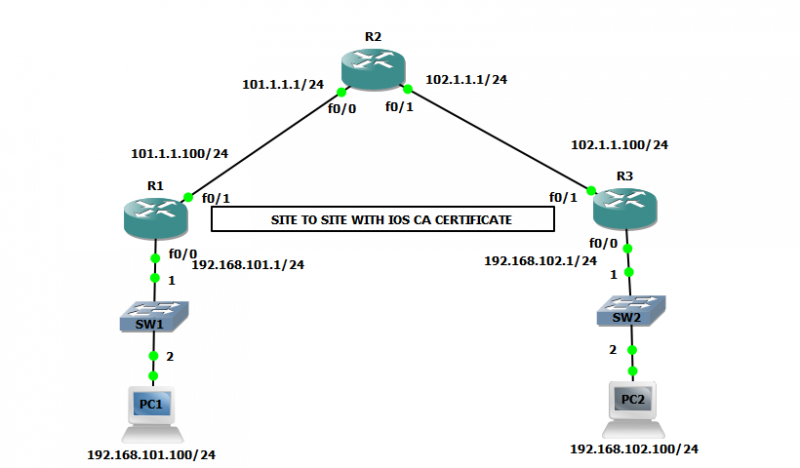
In our topology R1 and R3 are VPN peers, having PC1 and PC2 as end client which are going to communicate with each other using secure tunnel and R2 is the router, routing only public IP address.
Before VPN configuration we have made the VPN peers reachable to each other and DIGITAL CERTIFICATE has been enrolled by peers.
We are using
AES for encryption algorithm (for IKE phase 1 and IKE phase 2)
SHA as hashing algorithm (for IKE phase 1 and IKE phase 2)
Diffie-Hellman group 5
Name of the transform-set used CISCO-SET
Name of crypto map used CISCO-MAP
CONFIGURATION OF VPN AS FOLLOWS
On R1 in global configuration mode
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#authentication rsa-sig
R1(config-isakmp)#encryption aes
R1(config-isakmp)#hash sha
R1(config-isakmp)#lifetime 1800
R1(config-isakmp)#group 5
R1(config-isakmp)#exit
R1(config)#crypto ipsec transform-set CISCO-SET esp-aes esp-sha-hmac
R1(cfg-crypto-trans)#mode tunnel
R1(cfg-crypto-trans)#exit
R1(config)#crypto ipsec security-association lifetime seconds 1800
R1(config)#ip access-list extended 101
R1(config-ext-nacl)#permit ip 192.168.101.0 0.0.0.255 192.168.102.0 0.0.0.255
R1(config-ext-nacl)#exit
R1(config)#crypto map CISCO-MAP 10 ipsec-isakmp
R1(config-crypto-map)#set transform-set CISCO-SET
R1(config-crypto-map)#set peer 102.1.1.100
R1(config-crypto-map)#match address 101
R1(config-crypto-map)#exit
R1(config)#int f0/1
R1(config-if)#crypto map test
On R3 in global configuration mode
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#authentication rsa-sig
R1(config-isakmp)#encryption aes
R1(config-isakmp)#hash sha
R1(config-isakmp)#lifetime 1800
R1(config-isakmp)#group 5
R1(config-isakmp)#exit
R1(config)#crypto ipsec transform-set CISCO-SET esp-aes esp-sha-hmac
R1(cfg-crypto-trans)#mode tunnel
R1(cfg-crypto-trans)#exit
R1(config)#crypto ipsec security-association lifetime seconds 1800
R1(config)#ip access-list extended 102
R1(config-ext-nacl)#permit ip 192.168.102.0 0.0.0.255 192.168.101.0 0.0.0.255
R1(config-ext-nacl)#exit
R1(config)#crypto map CISCO-MAP 10 ipsec-isakmp
R1(config-crypto-map)#set transform-set CISCO-SET
R1(config-crypto-map)#set peer 101.1.1.100
R1(config-crypto-map)#match address 102
R1(config-crypto-map)#exit
R1(config)#int f0/1
R1(config-if)#crypto map test
I hope it solves your query. Its a basic practical and part of CCNP Security Certification syllabus. If you want to learn more about VPN technologies, you can prepare for CCNP Security and CCIE Security Certifications through some training institute or by self study.
thanks
- How can you guarantee a job for students who has no experience in Networking field?
- How to configure VPN between Cisco Router and ASA Firewall?
- How to configure RIPV2 with no auto summary?
- How to configure PAT (Port Address Translation)?
- How to configure Default Routing on Cisco Routers?
- What is the scope of CCNA course in India?
- What is scope of CCIE?
- How to remember 7 layers of OSI Model?
- How much salary can we get after doing CCNA course in Delhi Gurgaon?
- How many CCIE’s are there worldwide?
- Is it possible to pass CCIE Certification in 1st attempt?





