- Total 1 Answer
- 13377
Site to site on Router using pre-share keys with IKE Version-1
Topology used is following:
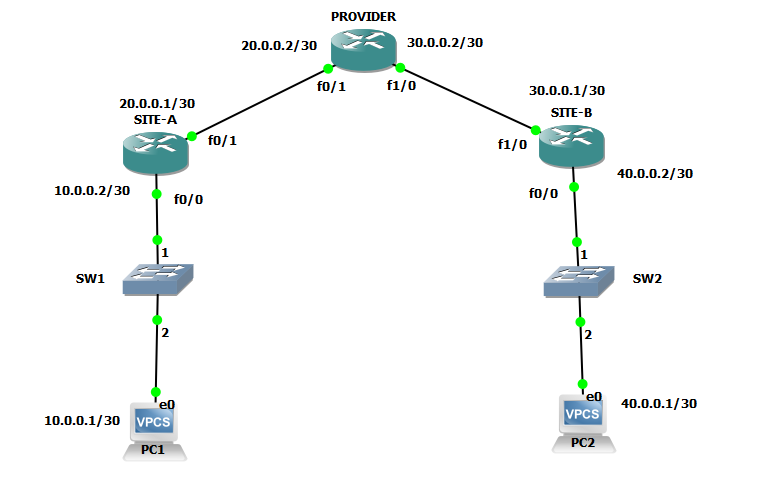
Commands with explanation:
On Router of SITE-A:
First thing we do is make IPsec phase-1 configuration by defining ISAKMP policy and parameters and priority to the policy (least is preferred always), Which will make ISAKMP SECURITY ASSOCIATION.
#crypto isakmp policy 1
In ISAKMP MODE with this command we define method of authentication of VPN peers.
#authentication pre-share
In ISAKMP MODE with this we define encryption algorithm to be used to encrypt phase-2 policies (Used Advance Encryption Standard).
#encryption aes
In ISAKMP MODE with this we define algorithm to be used for hashing (Used Secure Hashing Algorithm).
#hash sha
In ISAKMP MODE with this we define size of Diffie-Hellman shared secret key (Used group 5 means 1536 bit modulus).
#group 5
In ISAKMP MODE with this we define IPsec phase-1 lifetime in seconds (least is negotiated between peers).
#lifetime 1000
#exit
With this command we are defining pre-share-key, which peers will be using for authentication purpose and with what IP address peer will carry SA.
#crypto isakmp key BULLS address 30.0.0.1
With this we are configuring IPsec phase-2 (IPsec Security Association) parameters to be used these policy and parameters will be used to secure Data to be forwarded via IPsec VPN. We create Transform-set by giving it a name and define IPsec protocol to be used Encapsulating Security Payload/Authentication Header.
#crypto ipsec transform-set MY-SET esp-aes esp-sha-hmac
In transport mode we define the mode of IPsec which can be transport mode or tunnel mode which will define security will be provided up till L4 of OSI or up till L3 of OSI.
#mode tunnel
#exit
This command sets the lifetime for IPsec phase-2 (defined 200 seconds).
#crypto ipsec security-association lifetime seconds 200
With ACL we define interesting traffic which will use IPsec VPN. We will call this ACL in crypto map.
#access-list 100 permit ip 10.0.0.0 0.0.0.3 40.0.0.0 0.0.0.3
Now all these policy can’t be applied on exit interface directly, that is why we create crypto map by giving it a name (name define is MY-MAP) then we giving it a sequence number also provide ISAKMP profile to be used in IPsec.
#crypto map MY-MAP 1 ipsec-isakmp
Now in crypto map mode we call our transform set (calling MY-SET transform set).
#set transform-set MY-SET
In crypto map we also call ACL (calling ACL 100).
#match address 100
In crypto map we also call VPN peer’s IP (calling IP address of SITE-B).
#set peer 30.0.0.1
#exit
Now we apply this crypto map on interface by following commands to enable ISAKMP
#interface f0/1
#crypto map MY-MAP
Now we do similar configuration on SITE-B router by following commands:
On Router of SITE-B
#crypto isakmp policy 1
#authentication pre-share
#encryption aes
#hash sha
#group 5
#lifetime 1000
#exit
#crypto isakmp key BULLS add 20.0.0.1
#crypto ipsec transform-set MY-SET esp-aes esp-sha-hmac
#mode tunnel
#exit
#crypto ipsec security-association lifetime seconds 200
#access-list 100 permit ip 40.0.0.0 0.0.0.3 10.0.0.0 0.0.0.3
#crypto map MY-MAP 1 ipsec-isakmp
#set transform-set MY-SET
#match address 100
#set peer 20.0.0.1
#exit
#interface f0/1
#crypto map MY-MAP
Hope you have got your query resolved related to S2S VPN. For further more questions please put your comments or Ask another question. This topic is related to CCIE Security Course.
- How can you guarantee a job for students who has no experience in Networking field?
- How to configure VPN between Cisco Router and ASA Firewall?
- How to configure RIPV2 with no auto summary?
- How to configure PAT (Port Address Translation)?
- How to configure Default Routing on Cisco Routers?
- What is the scope of CCNA course in India?
- What is scope of CCIE?
- How to remember 7 layers of OSI Model?
- How much salary can we get after doing CCNA course in Delhi Gurgaon?
- How many CCIE’s are there worldwide?
- Is it possible to pass CCIE Certification in 1st attempt?





